Why would I want to use MSIX and what is it?
Do you have a bloated application? Maybe one or two that are so old it doesn’t even have any install parameters? Maybe you have a massive application that is a pain to deploy?
Well MSIX might be for you! Wrapping your app with MSIX sounds fine and dandy however you need to also create a certificate otherwise you won’t be able to deploy the app properly. I’ll walk you through the setup from start to finish.
Prerequisites
Microsoft Store for Business configured
-The first person to sign in to Microsoft Store for Business must be a Global Admin of the Azure Active Directory (AD) tenant. Once the Global Admin has signed in, they can give permissions to others employees.
A machine that can run Hyper-V
Getting your certificate and deploying it
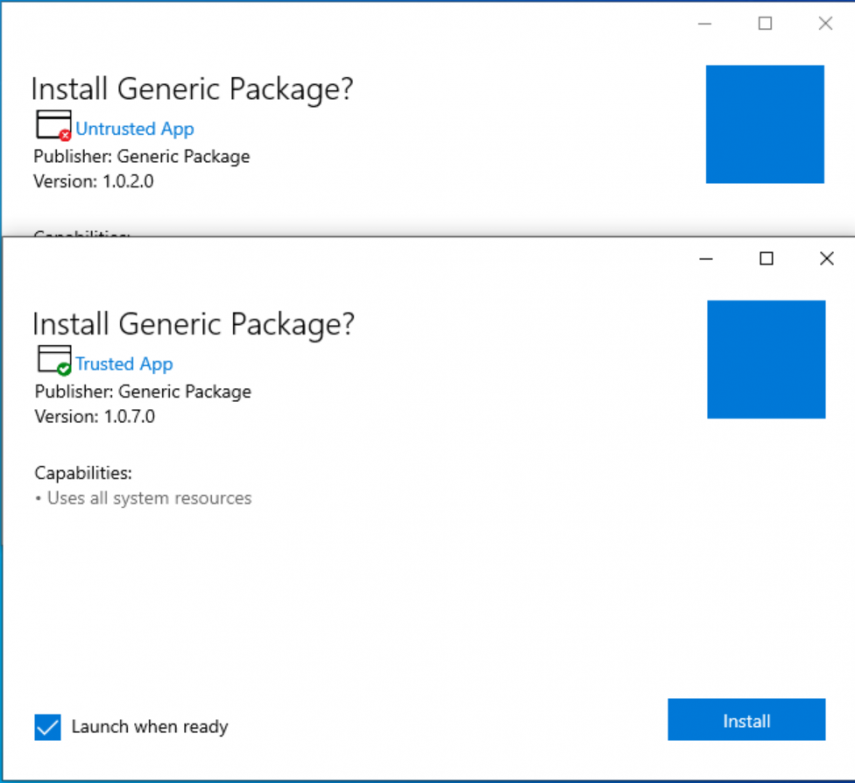
The reason we need to get a certificate is to make the app a trusted one. Once we have this in place the app will go from Untrusted to Trusted like the picture below
- Log in to Microsoft Store for Business
- Select Manage
- Select Settings
- Select Devices
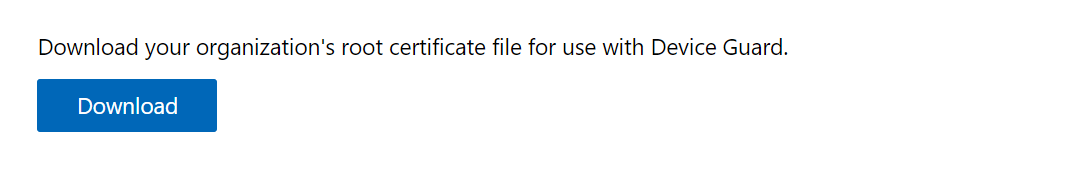
- Select Download on Download your organization’s root certificate file for use with Device Guard
You will need to deploy this certificate to any machine that you want to install the app on so let’s create the Intune Configuration Profile for it
- Log in to Device Management
- Select Devices
- Select Configuration Profiles
- Select Create Profile
- Select Windows 10 and later
- Select Trusted Certificate
- Select Create
- Give the certificate profile a name
- Select Next
- Browse to your certificate file
- Select Next
- Assign to any group that needs to install the application
- Select Next
- Select Next
- Select Create
Now you have the certificate and it’s deployed to your users/devices! Lets get to packaging our apps!
Creating your packaging environment
- Launch Hyper-V Manager
- Select Quick Create…
- Select MSIX Packaging Tool Environment
- Select Create Virtual Machine
This will start the creation process of your image. It will take some time to download and setup. Once setup I strongly recommend right clicking the Virtual machine and Checkpointing it if you want to do multiple apps.
Packaging your app
- Launch the MSIX Packaging Tool on the Virtual machine
- Select environment - Leave default and select Next
- Prepare computer - Select Next
- Select Installer - Browse to your installer EXE
- Specify install arguments if you’d like (Optional)
- Signing Preference should be set to Sign with Device Guard Signing
- Select the Sign in with Microsoft button (Sign in with an admin account)
- Select Next
- Package Information - Fill in all required fields and select Next
- Installation - Your app will begin to install, run through the installation and select Next
- First Launch Tasks - Select Next
- Select Yes, Move on
- Services report - Select Next
- Create package - Select Create
- Select Close to the popup
Adding your MSIX to Intune
- Log in to Device Management
- Select Apps
- Select Windows
- Select Add
- App type set to Line-of-business app
- Select Select
- Select the MSIX Package we created
- Verify that all the information looks correct and add a Logo if desired
- Select Next
- Add User/Device assignments
- Select Next
- Select Create
Congrats! You have a deployed app now! I strongly recommend rebooting the machine after the certificate is deployed and then attempting the installation but you should be all set!
Jake Shackelford Admin/Contributor
Jake is one of our Admins but also our inaugural author and the main reason SysManSquad exists today.